What is Neurosecurity?
Originally used to refer to the security of neural devices,[1] we define neurosecurity as the application of neuroscience to behavioral information security to better understand and improve users’ security behaviors.[2] One ultimate goal of neurosecurity is to design more effective user interfaces (UIs) that can help users make informed decisions.
Recent News
Research Team

Bonnie Brinton Anderson ( ) is the Douglas & Effie Driggs Professor of Information Systems in the Marriott School of Business at Brigham Young University. She received her PhD from Carnegie Mellon University. Her work has been published in Information Systems Research, Journal of Management Information Systems, Journal of the Association for Information Systems, European Journal of Information Systems, Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Decision Support Systems, Electronic Commerce Research, Expert Systems with Applications; Electronic Commerce Research, Communications of the ACM, Information Sciences, IEEE Transactions: Systems, Men, and Cybernetics, The Journal of Systems and Software, and other outlets. She currently researches the intersection of decision neuroscience and behavioral information security.

Jeff Jenkins ( ) is a Professor of Information Systems at the Marriott School of Business, Brigham Young University. He graduated with a Ph.D. in Management Information Systems from the University of Arizona. His active research includes human-computer interaction and behavioral information security. In a human-computer interaction context, Jeff’s research explores how to infer human states using computer input devices such as the computer mouse, keyboard, or touchscreen. His research has been published in various journals and conference proceedings, including MIS Quarterly, Information Systems Research, Journal of Management Information Systems, Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Computers in Human Behavior, and others. Prior to earning his Ph.D., Jeff was a Software Engineer in both the public and private sectors.

C. Brock Kirwan ( ) is the Director of the MindCORE Neuroimaging Facility at the University of Pennsylvania. He received his PhD in Psychological and Brain Sciences from Johns Hopkins University in 2006. Dr. Kirwan has a decade of experience conducting fMRI scans with patient populations at Johns Hopkins University, the University of California, San Diego, the University of Utah, BYU, and now the Univeristy of Pennsylvania. He has published numerous papers reporting fMRI and neuropsychological results in journals such as Science, Proceedings of the National Academy of Sciences, Neuron, the Journal of Neuroscience, as well as information systems journals such as Information Systems Research, Journal of Management Information Systems, Journal of the Association for Information Systems, and European Journal of Information Systems.

Anthony Vance ( ) is a professor and Commonwealth Cyber Initiative Fellow in the Department of Business Information Technology of the Pamplin College of Business at Virginia Tech. He earned Ph.D. degrees in Information Systems from Georgia State University, USA; the University of Paris—Dauphine, France; and the University of Oulu, Finland. Previous to his PhD studies, he worked as a cybersecurity consultant at Deloitte. His research focuses on how to help individuals and organizations improve their cybersecurity posture, particularly from behavioral, organizational, and neuroscience perspectives. His work is published in outlets such as MIS Quarterly, Information Systems Research, Journal of Management Information Systems, Journal of the Association for Information Systems, Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Workshop on the Economics of Information Security (WEIS), and the Symposium on Usable Privacy and Security (SOUPS). He currently is a senior editor at MIS Quarterly. .
Affiliated Researchers

David Eargle ( ) is a cybersecurity consultant. He earned his Ph.D. degree in Information Systems from the University of Pittsburgh. His research interests include human-computer interaction and information security. He has coauthored several articles in these areas using neurophysiological and other methodologies in outlets such as Information Systems Research, Journal of Management Information Systems, Journal of the Association for Information Systems, European Journal of Information Systems, the International Conference on Information Systems, and the Hawaii International Conference on System Sciences, along with the Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI).
Research Agenda
This TED-style presentation at USENIX Enigma 2017 summarizes the research of the BYU Neurosecurity Lab.
We also have published a research agenda for using neurosecurity to study security messages. The purpose of our research agenda is to highlight the promise of using neurophysiological measures, and encourage more research in this area.Research Methods
The below 10-minute video gives an overview of fMRI and how it can be used to research security and privacy behavior. The presentation was given at the Symposium on Usable Privacy and Security (SOUPS) 2015.
Overview of Neurocognitive Methods
Although neurosecurity is new to the field of information systems, there is a wide range of well-established neurocognitive methods from the field of neuroscience. We summarize below some of the most prominent methods.[3-5]
| Image | Neurocognitive Tool | Focus of Measurement | Strengths | Weaknesses | ||
|---|---|---|---|---|---|---|
|
|
Eye Tracking | Eye pupil location ('gaze') and movement | Identify visual activity; clear visualization of what was viewed at any given moment | Doesn't capture peripheral vision; can't ensure gaze equates with thought or attention; artificial setting may bias behavior. | ||

|
Skin conductance response (SCR) or electrodermal activity (EDA) | Sweat in eccrine glands of the palms or feet | Low cost; easy to use; minimal intervention on subjects | Lack of predictable measurement; habituation; still some debate on interpretation | ||

|
Facial electromyography (fEMG) | Electrical impulses on face caused by muscle fibers | High degree of precision, widely accessible, minimally invasive | Only a small number of muscles can be measured; difficulty with interpretation; setting may bias behavior | ||
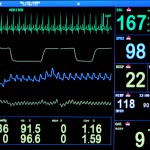
|
Electrocardiogram (ECG or EKG) | Electrical activity on skin caused by muscles of the heart | Minimally invasive; low cost; widely accessible | Heart rate may be affected by a wide variety of factors | ||
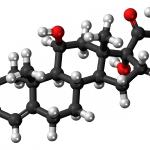
|
Cortisol | Level of cortisol (commonly called the stress hormone) in one’s bloodstream or saliva. | Minimally invasive; low cost | Cortisol levels peak 10–40 minutes after stressor onset | ||
|
|
Mouse-cursor tracking | The cursor location and movement properties on the screen | Inexpensive; noninvasive; mass-deployable; useful in natural and non-laboratory settings; surrogate for attention; changes in movement precision correlate with emotional changes | Can’t capture attention if the mouse cursor is not moving. Can’t ensure movement equates with thought or attention. | ||
| Brain imaging tools | ||||||

|
Functional magnetic resonance imaging (fMRI) | Blood flow changes (BOLD response) in the brain due to neural activity | Noninvasive; standard data analysis methods; spatial resolution | Artificial setting; temporal resolution (few seconds’ delay); need to be careful with correlation vs. causation | ||

|
Positron emission tomography (PET) | Metabolic changes in the brain due to neural activity | Spatial resolution | Invasive (due to injected tracer); potentially harmful; low temporal resolution (2–3 minutes) | ||

|
Electroencephalography (EEG) | Electrical potentials on the scalp due to neural activity | Inexpensive; tolerant of a little subject motion; directly measures electrical activity; temporal resolution in milliseconds | Spatial resolution; only sensitive to outer layers of cortex | ||

|
Magnetoencephalography | Magnetic field changes due to neural activity | Temporal resolution in milliseconds; deeper capability than EEG | Spatial resolution | ||

|
Transcranial magnetic stimulation (TMS) | Weak electrical current causes activity in specific parts of the brain—measure activity and function of specific connections/pathways | Noninvasive; less expensive than fMRI | Can only stimulate 2 in. deep; may induce seizure or fainting | ||

|
Functional near-infrared spectroscopy (fNIR) | Blood flow changes (BOLD response) in the brain due to neural activity | Noninvasive; less expensive and more portable than fMRI | Can only measure cortical activity 4 cm deep | ||
Related Work
Below is a listing of publications authored by the BYU Neurosecurity Lab:
- Jenkins, J., Anderson, B., Vance, A., Kirwan, B., Eargle, D. “More Harm than Good? How Security Messages that Interrupt Make Us Vulnerable,” Information Systems Research, 27 (4), pp. 880–896..
- Anderson, B., Vance, A., Kirwan, B., Eargle, D., Jenkins, J., “How Users Perceive and Respond to Security Messages: A NeuroIS Research Agenda and Empirical Study,” European Journal of Information Systems, forthcoming.
- Anderson, B., Kirwan, B., Eargle, D., Jensen, S., Vance, A. 2015. “Neural Correlates of Gender Differences and Color in Distinguishing Security Warnings and Legitimate Websites: A Neurosecurity Study,” Journal of Cybersecurity, 1 (1), pp. 109–120.
- Anderson, B., Kirwan, B., Eargle, D., Howard, S., Vance, A. 2015. “How Polymorphic Warnings Reduce Habituation in the Brain—Insights from an fMRI Study,” Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Seoul, Korea, pp. 2883–2892.
- Anderson, B., Vance, A., Kirwan, B., Eargle, D., Howard, S. 2014. “Users Aren’t (Necessarily) Lazy: Using NeuroIS to Explain Habituation to Security Warnings,” International Conference on Information Systems, Auckland, New Zealand.
- Vance, A., Anderson, B., Kirwan, B., Eargle, D. 2014. “Using Measures of Risk Perception to Predict Information Security Behavior: Insights from Electroencephalography (EEG),” Journal of the Association for Information Systems, 15 (10), pp. 679–722.
- Anderson, B., Vance, A., Kirwan, B., Eargle, D., Howard, S. 2014. “Why Users Habituate to Security Warnings: Insights from fMRI,” The Dewald Roode Workshop on Information Systems Security Research, IFIP WG8.11/WG11.13, Newcastle, UK.
- Anderson, B., Vance, A., Eargle, D. 2013. “Is Your Susceptibility to Phishing Dependent on Your Memory?,” Workshop on Information Security & Privacy, AIS SIGSEC and IFIP TC11.1, Milan, Italy.
- Anderson, B., Vance, A., Eargle, D., Brock, K. 2013. “Your Memory is Working Against You: How Eye Tracking and Memory Explain Susceptibility to Phishing,” The Dewald Roode Workshop on Information Systems Security Research, IFIP WG8.11/WG11.13, Niagara, NY.
- Anderson, B., Vance, A., Hansen, J., Kirwan, B., Eargle, D., Hinkle, L., Weagel, A. 2012. “Neural Correlates of Gender Differences in Distinguishing Malware Warnings and Legitimate Websites: A NeuroIS Study,” The Dewald Roode Workshop on Information Systems Security Research, IFIP WG8.11/WG11.13, Provo, UT.
Below is a listing of neurosecurity publications by other authors:
- Neupane, A., Saxena, N., Maximo, J., and Kana, R. "Neural Markers of Cybersecurity: An fMRI Study of Phishing, and Malware Warnings." IEEE Transactions on Information Forensics and Security (TIFS), forthcoming.
- Warkentin, M., Walden, E., Johnston, A.C., and Straub, D. “Neural Correlates of Protection Motivation for Secure IT Behaviors: An fMRI Exploration,” Journal of the Association of Information Systems, 17 (3), pp. 194–215.
- Neupane, A., Rahman, M.L., Saxena, N., Hirshfield, L. 2015. "A Multi-Modal Neuro-Physiological Study of Phishing Detection and Malware Warnings," Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS), Denver, CO, pp. 479–491.
- Hu, Q., West, R. and Smarandescu, L. 2015. “The Role of Self-Control in Information Security Violations: Insights from A Cognitive Neuroscience Perspective,” Journal of Management Information Systems, 31 (4), pp. 6–48.
- Neupane, A., Saxena, N., Kuruvilla, K., Georgescu, M., and Kana, R. 2014. Neural Signatures of User-centered Security: An fMRI Study of Phishing, and Malware Warnings. Proc. NDSS, pp. 1–16.
- Hu, Q., West, R., Smarandescu, L., and Yaple, Z. (2014) “Why Individuals Commit Information Security Violations: Neural Correlates of Decision Processes and Self- Control.” Proceedings of the 47th Hawaii International Conference on Systems Science (HICSS 2014), January 6-9, Hawaii, USA.
Footnotes
- Denning, Tamara, Matsuoka, Yoky, Kohno, Tadayoshi. 2009. "Neurosecurity: Security and Privacy for Neural Devices,” Neurosurgical Focus, 27 (1), pp. 1-4.
- Anderson, Bonnie Brinton., Kirwan, C. Brock, Eargle, David., Howard, Seth, Vance, Anthony. “How Polymorphic Warnings Reduce Habituation in the Brain—Insights from an fMRI Study,” Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Seoul, Korea, 2015.
- Dimoka, Angelika. 2012. "How to Conduct a Functional Magnetic Resonance (fMRI) Study in Social Science Research." MIS Quarterly, 36 (3), pp. 811-840.
- Riedl, René, Davis, Fred, Hevner, Alan R. 2014. "Towards a NeuroIS Research Methodology: Intensifying the Discussion on Methods, Tools, and Measurement," Journal of the Association for Information Systems, 15 (10), pp. i-xxxv.
- Dimoka, Angelika, Banker RD, Benbasat, I, Davis, F, Dennis, AR, Gefen, D., et al. 2012. "On the Use of Neurophysiological Tools in IS Research: Developing a Research Agenda for NeuroIS," MIS Quarterly, 36 (3), pp. 679-702.
 ≠
≠